One of the most dangerous scams making the rounds is an email that appears to come from someone you know—a neighbor, friend, or even a family member. The message might say something like “RSVP for the celebration (of life)” ,“Click here to view the invitation.”, “Check out this important document” or “Check out the pictures”.
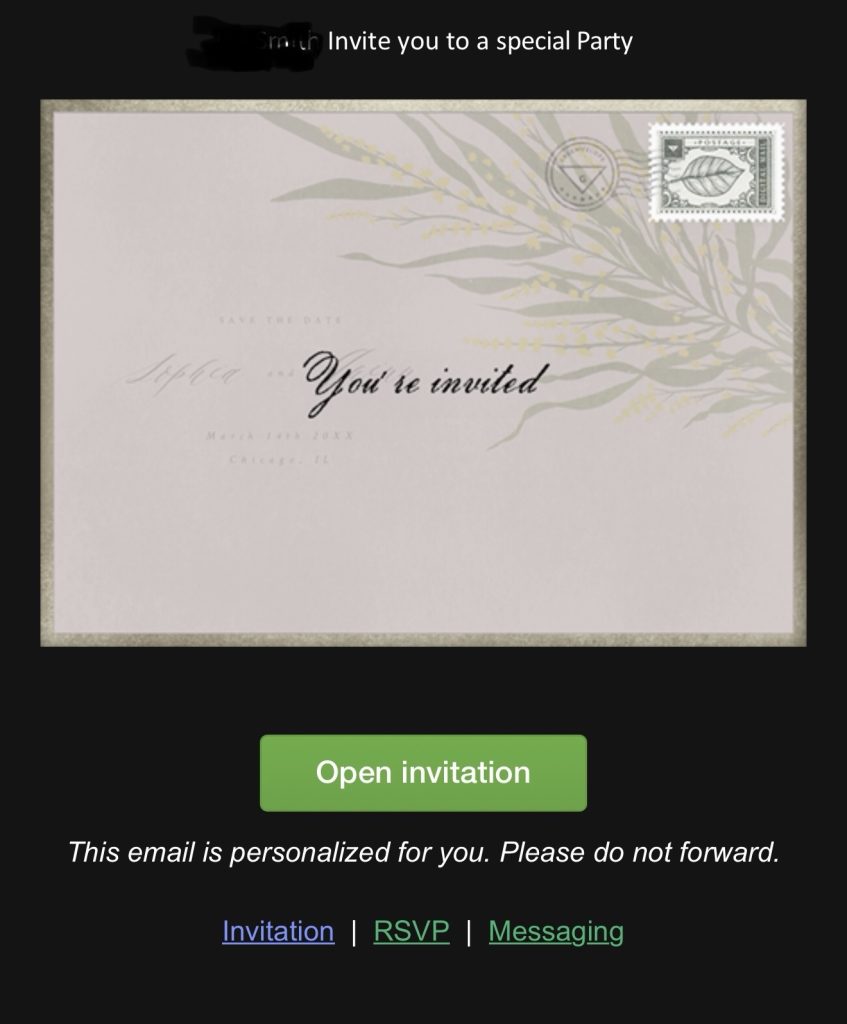
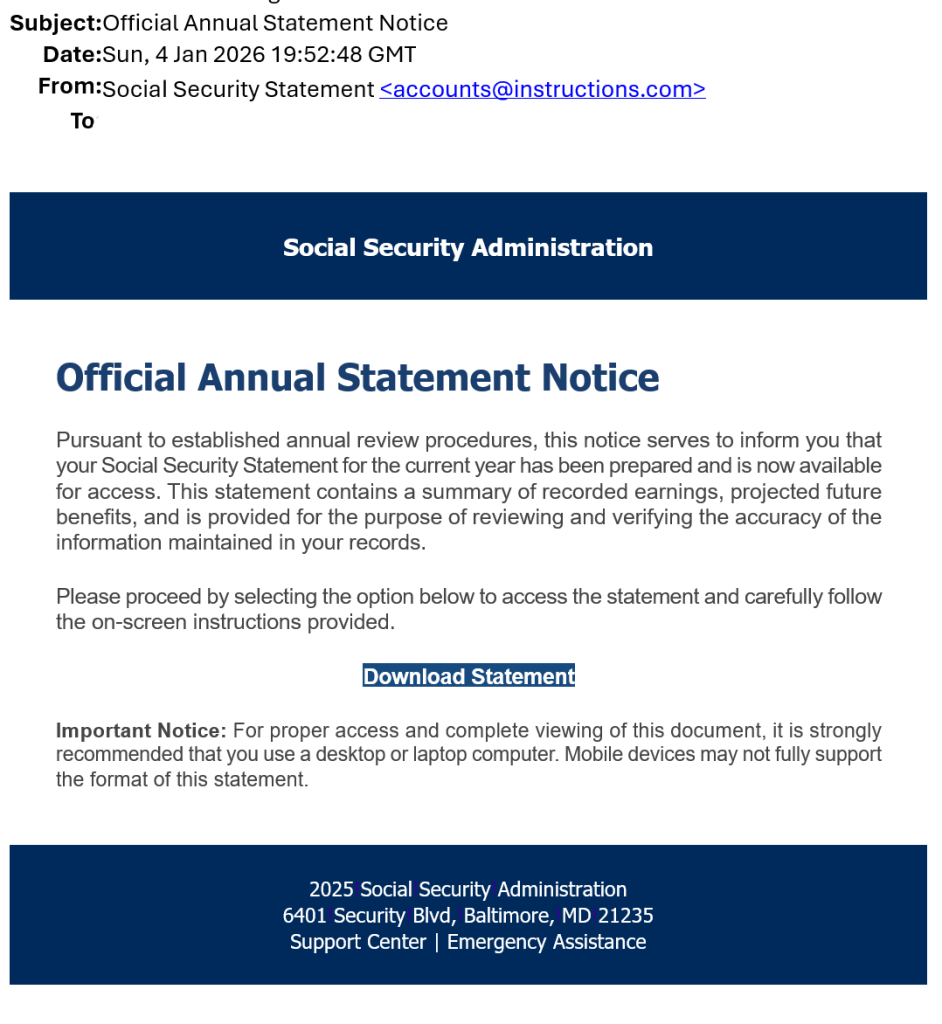
If you click the link, it discreetly downloads a remote access tool onto your computer. Once installed, scammers can take control of your system, access your online accounts, steal data, or even lock you out completely. They wait for you to step away from your computer, or the middle of the night when you’re asleep. They go through your web browser, password manager and files. If they can access your financial institutions they may attempt to transfer money out. If they can access your Amazon or other online shopping accounts, they may try to purchase gift cards using your saved payment information. If they can access your email, they may intercept account sign in links and codes, make a copy of your address book, and use your email address and/or familiar name to send a similar “invitation” to your contacts in hopes to scam others.
[Read more…]